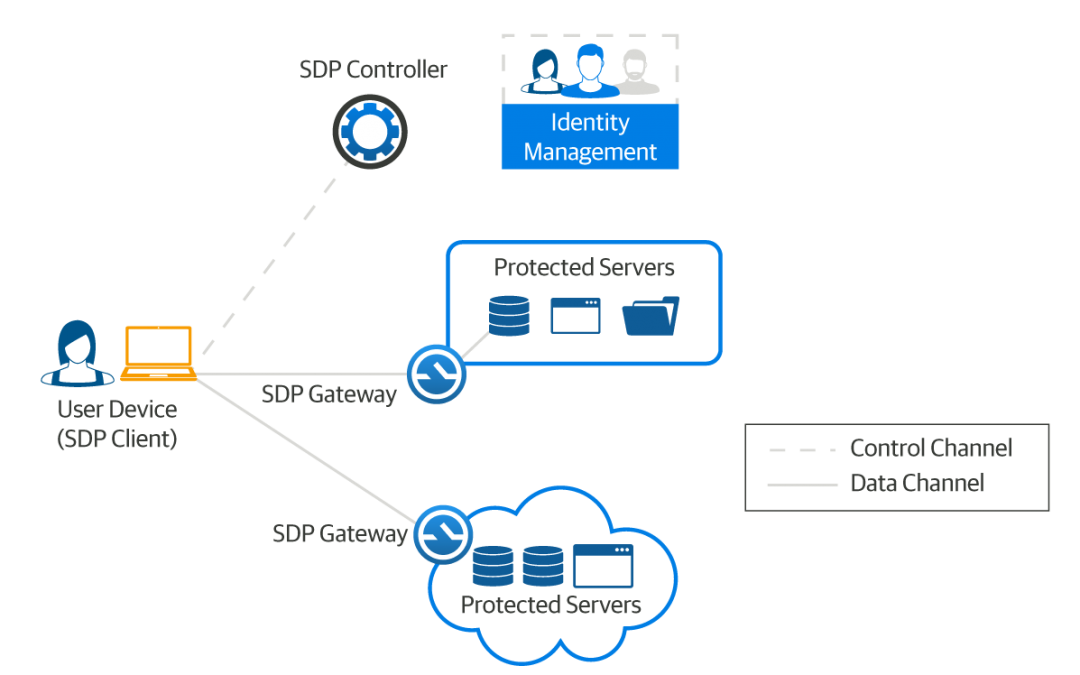
The basic premise of a Software-Defined Perimeter (SDP) is built on an “authenticate first, connect second” approach. Unlike a traditional network that connects various roles or groups to a network segment and then relies on application level permissions for authorization, a Software-Defined Perimeter creates individualized perimeters for each user, allowing for much more fine grained access control.
Using your own home as an example, imagine someone is knocking on your front door. The Software-Defined Perimeter zero-trust approach takes the person that is knocking at your front door, confirms who the person is and what it is that they want/ need, and then opens the door to let them inside of the house. Once inside the house, they can only access those rooms that they need, and nothing else. Simple right?
Infinitely adjustable, as a user’s situation changes, their individualized security perimeter changes also. Software-Defined Perimeters control access to network resources that are across hybrid environments – in a corporate datacenter or in the cloud – meaning that consistent access policies can be enforced. SDP addresses cyber-attacks, compliance and cloud migration as well as overcoming the challenges around specific types of cyber-attacks, compliance and scope reduction.
To download the definitive guide to Software-defined perimeter click here



Recent Comments